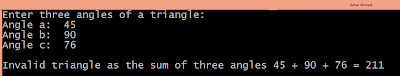
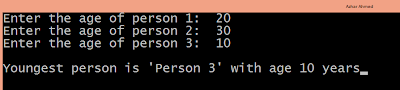
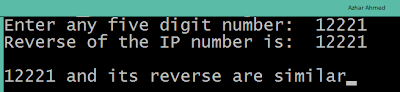
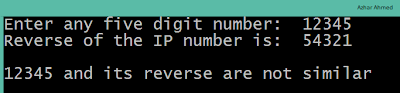
Converter program :
Centimeter-->Inches
Litre-->Gallon
Kilometer-->Miles
Kilogram-->Pounds
This is the code:
#include<iostream.h>
#include<stdio.h>
void main()
{
printf("This is the menu:\n\n");
cout<<" Inch<--> Centimeter\nGallon<-->Litres\nMile<-->Kilomemter\nPound<-->Kilogram\n\n";
cout<<"Now acording to your choice: select it\n";
cout<<"inch->centimeter press 1\nCentimetr->inch press 2\nLitr->Gallon press 3\nGallon->Litre press 4\n";
cout<<"Mile->Kilometr press 5\nKilomter->Mile press 6\nPound->Kilogram press 7\nKilogram->pound press 8\n\n";
int a;float z,b;
cin>>a;
switch(a)
{
case 1:
cout<<"Enter your unit value\n";
cin>>z;
b=z*2.54;
cout<<"\nThis is the conversion result of inch to centimeter\n"<<b<<endl;
case 2:
cout<<"Entr your unit value:\n";
cin>>z;
b=(1.0/2.54)*z;
cout<<"This is the conversion result of Centimeter to inch\n"<<b<<endl;
case 3:
cout<<"Entr your unit value:\n";
cin>>z;
b=z*3.785;
cout<<"\nThis is the conversion of Gallon to Litre\n"<<b<<endl;
case 4:
cout<<"Enter your unit value:\n";
cin>>z;
b=(1.0/3.785)*z;
cout<<"This is the conversion result of Litre to Gallon\n"<<b<<endl;
case 5:
cout<<"Enter your unit value:\n";
cin>>z;
b=z*1.609;
cout<<"This is the conversion of Mile to Kilometers\n"<<b<<endl;
case 6:
cout<<"Enter your unit value:\n";
cin>>z;
b=(1.0/1.609)*z;
cout<<"This is the conversion of Kilometer to Mile\n"<<b<<endl;
case 7:
cout<<"Enter your unit value:\n";
cin>>z;
b=z*.4536;
cout<<"This is the conversion of Pound to Kilogram\n"<<b<<endl;
case 8:
cout<<"Enter your unit value:\n";
cin>>z;
b=(1.0/.4536)*z;
cout<<"This is the conversion of Kilogram to pound\n"<<b<<endl;
default:
cout<<"Please try again and enter a valid option\n";
}
}
Centimeter-->Inches
Litre-->Gallon
Kilometer-->Miles
Kilogram-->Pounds
This is the code:
#include<iostream.h>
#include<stdio.h>
void main()
{
printf("This is the menu:\n\n");
cout<<" Inch<--> Centimeter\nGallon<-->Litres\nMile<-->Kilomemter\nPound<-->Kilogram\n\n";
cout<<"Now acording to your choice: select it\n";
cout<<"inch->centimeter press 1\nCentimetr->inch press 2\nLitr->Gallon press 3\nGallon->Litre press 4\n";
cout<<"Mile->Kilometr press 5\nKilomter->Mile press 6\nPound->Kilogram press 7\nKilogram->pound press 8\n\n";
int a;float z,b;
cin>>a;
switch(a)
{
case 1:
cout<<"Enter your unit value\n";
cin>>z;
b=z*2.54;
cout<<"\nThis is the conversion result of inch to centimeter\n"<<b<<endl;
case 2:
cout<<"Entr your unit value:\n";
cin>>z;
b=(1.0/2.54)*z;
cout<<"This is the conversion result of Centimeter to inch\n"<<b<<endl;
case 3:
cout<<"Entr your unit value:\n";
cin>>z;
b=z*3.785;
cout<<"\nThis is the conversion of Gallon to Litre\n"<<b<<endl;
case 4:
cout<<"Enter your unit value:\n";
cin>>z;
b=(1.0/3.785)*z;
cout<<"This is the conversion result of Litre to Gallon\n"<<b<<endl;
case 5:
cout<<"Enter your unit value:\n";
cin>>z;
b=z*1.609;
cout<<"This is the conversion of Mile to Kilometers\n"<<b<<endl;
case 6:
cout<<"Enter your unit value:\n";
cin>>z;
b=(1.0/1.609)*z;
cout<<"This is the conversion of Kilometer to Mile\n"<<b<<endl;
case 7:
cout<<"Enter your unit value:\n";
cin>>z;
b=z*.4536;
cout<<"This is the conversion of Pound to Kilogram\n"<<b<<endl;
case 8:
cout<<"Enter your unit value:\n";
cin>>z;
b=(1.0/.4536)*z;
cout<<"This is the conversion of Kilogram to pound\n"<<b<<endl;
default:
cout<<"Please try again and enter a valid option\n";
}
}